.jpg)
Proud nominee for the SANS Difference Maker Awards 2025 — Innovation of the year finalist!
3 months to 30 minutes
Security
Architecture.
Review
Done Fast. Done well.
Because when reviews take months, the product has already moved on.

What If Security Review Isn’t a Nightmare?
You’d actually look forward to security reviews — crazy, right?
From Months to Minutes
Upload your product specifications, architecture notes, docs, or security policies (no diagrams required). SecurityReview.ai uses your real documentation to run a complete standards-aligned security design review.


Compliance Mapping
SecurityReviewa.ai automatically aligns threats and mitigations with leading compliance frameworks, producing audit-ready reports that simplify regulatory requirements.

Code-First Reviews
Drop in your source code. We surface the structure, spot the issues, and give you a full review with zero documentation required.

Built for Your Workflow
Pulls in content from Jira, Teams, Slack, Confluence, Google Docs, GitHub, and ServiceNow while also supporting voice recordings. You don’t need to switch platforms or create anything new just to get started.


Flexible Review Scope
Zoom in on a single feature or scan your whole system. Run a security checkup as quick as a sprint or as deep as a full-body scan, all on your terms.

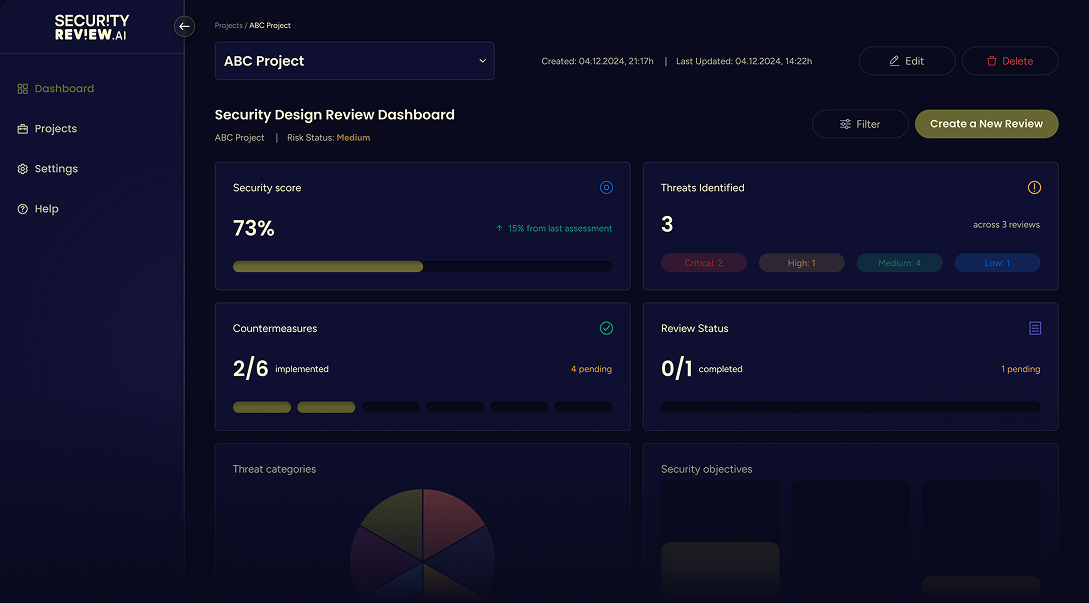
Participative and Question-Based Threat Modeling
The interactive questioning engine enables team members to collaboratively answer clarifying questions, making threat modeling more accurate, inclusive, and grounded in real-world context.


Human-in-the-Loop by Design
Every step is editable, so you can review, tweak, and validate before anything gets locked in. Even role designations and responsibilities can be adjusted (by you) at every stage.


A Standardized Approach to Security Design Review
Every team follows the same process, so nothing is overlooked. You don’t have to build a new model every time. Just use existing architecture docs, product specs, and security policies, even tribal knowledge from your teams, and we’ll use the same steps, the same logic, and the same structure for every review.


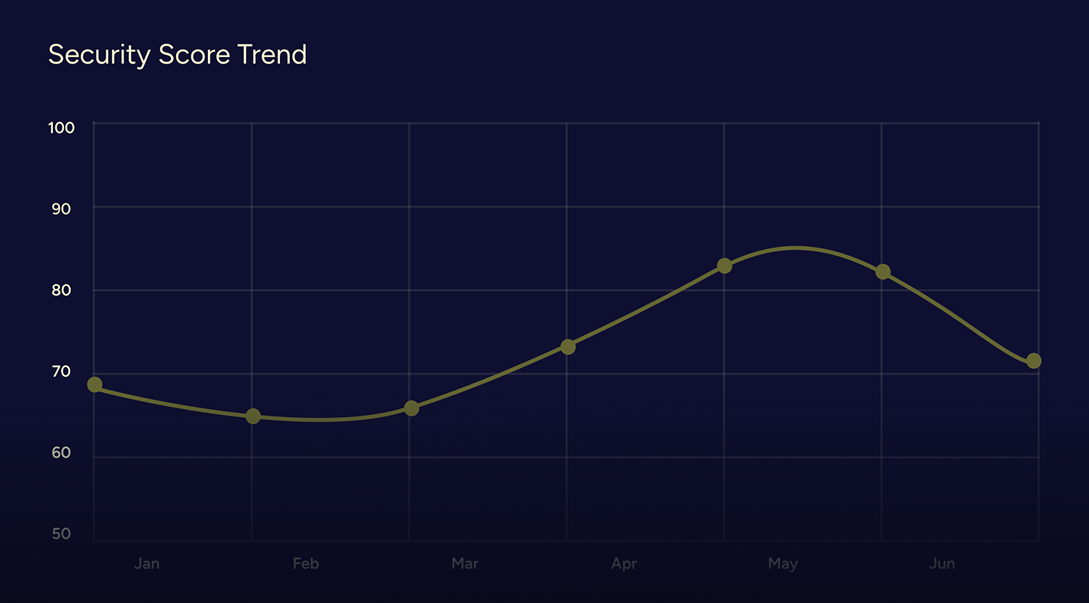
Get the Right Fix to the Right Person
See exactly what’s risky, why it matters, and who should handle it. Findings are written in plain language, prioritized by impact, and mapped to the right role. As fixes are made, everything stays trackable, so nothing gets lost, and progress stays visible.



.webp)
%20copy%201.png)

